Permissions and Security Roles in Dynamics 365 CRM
Understanding Permissions and Security Roles in Dynamics 365 CRM
Managing access to data and functionality is crucial for maintaining data integrity, ensuring compliance, and protecting sensitive information in any CRM system. Microsoft Dynamics 365 CRM (D365 CRM) provides a robust framework for managing permissions through security roles. This article explains the concepts of permissions and security roles in D365 CRM, highlighting their importance and offering effective management strategies.
What Are Permissions in D365 CRM?
Permissions in D365 CRM control what users can see and do within the system. They define the level of access a user has to different records and functionalities, allowing or restricting access at various levels:
- Record-level access: Determines which records a user can view or modify.
- Field-level access: Controls which fields within a record a user can view or edit.
- Action-level access: Governs user actions on records, such as create, read, update, delete (CRUD operations), assign, and share.
Security Roles: The Backbone of Permissions
Security roles in D365 CRM are collections of permissions that define a user’s access and capabilities within the system. Each security role specifies access levels for various entities:
- Core Records: Fundamental entities like accounts, contacts, opportunities, and leads.
- Marketing: Entities for marketing activities, such as campaigns and marketing lists.
- Sales: Entities specific to sales processes, like quotes, orders, and invoices.
- Service: Entities used in customer service, such as cases, entitlements, and service activities.
- Customization: Permissions for customizing the system, including modifying entities, fields, forms, and views.
- Business Management: Permissions for managing business units, teams, and users.
How Security Roles Work
When a user logs into D365 CRM, the system checks assigned security roles to determine data and functionality access. Security roles accumulate, meaning users can have multiple roles whose permissions combine for their effective access.
Key Features of Security Roles:
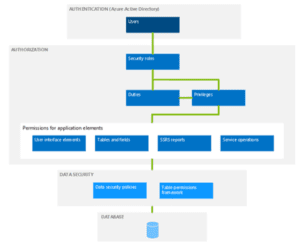
Security roles hierarchy
- Role-based security: Users receive roles based on job functions, ensuring tailored access.
- Hierarchical security: Access levels can follow hierarchies, granting higher roles (e.g., managers) greater permissions than lower roles (e.g., team members).
- Field security profiles: Profiles restrict access to specific entity fields, adding another layer of security.
- Team-based security: Users grouped into teams can have roles assigned collectively, simplifying permissions management for large groups.
Best Practices for Managing Permissions and Security Roles
- Principle of Least Privilege: Assign users minimal access necessary for their roles, reducing unauthorized data exposure.
- Regular Review and Audit: Periodically review and update roles and permissions to match current business needs and standards.
- Segregation of Duties: Separate critical functions among roles to prevent conflicts and minimize fraud risks.
- User Training: Educate users on security role importance and proper access utilization.
- Use Default Roles as Templates: Customize D365 CRM’s default roles to align with specific organizational needs.
Conclusion
Permissions and security roles are fundamental to Microsoft Dynamics 365 CRM’s security model. By managing these elements thoughtfully, organizations ensure data security, compliance, and access control. Adhering to best practices supports efficient CRM operations and safeguards sensitive information effectively.

